Free Nitro - NahamCon CTF 2022
This was actually the first time seeing the category "Malware" in a CTF. I did not solve this challenge during the ctf but figgured out how to solve it afterwards.
Challenge
As you can see the challenge had quiete a few solves. After the ctf I found out, there is an easy way to solve this challenge. I am not sure if this was intended but since this would be to easy for a medium challenge I don't think so.
Solving it the easy way
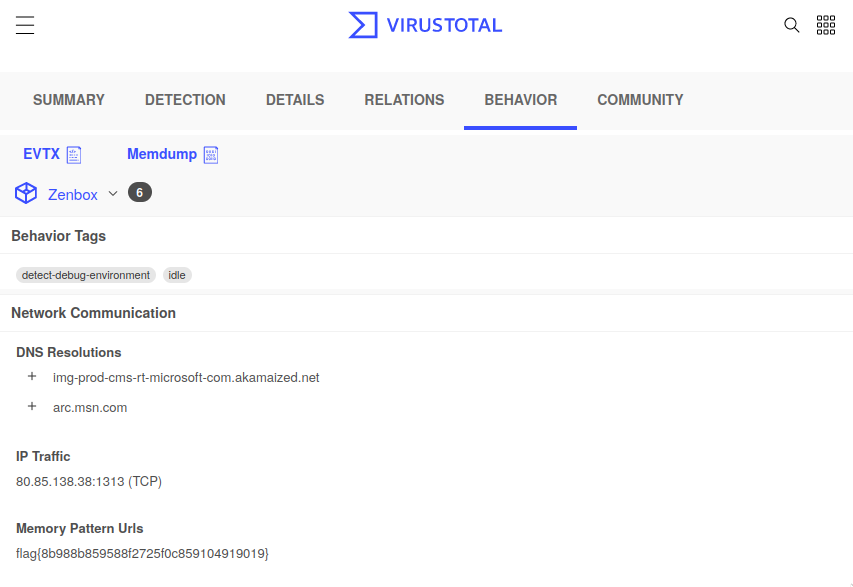
Turns out you just have to upload the file to VirusTotal and check the behavior report.
Not solving it the hard way
The challenge proviedes us with a single Windows executable. file tells us that we got a .Net executable so lets fire up dnSpy and throw it in there.
$ file free_nitro.exe
free_nitro.exe: PE32+ executable (GUI) x86-64 Mono/.Net assembly, for MS Windows.Net is compiled to Common Intermediate Language (CIL) which can be decompiled back to a high level language like C#. This makes things a bit easier
to read. After having a short look at the code it was clear, that this executable is some kind of loader for some encrypted content.
I noticed a decrypt function which sounds prommising.
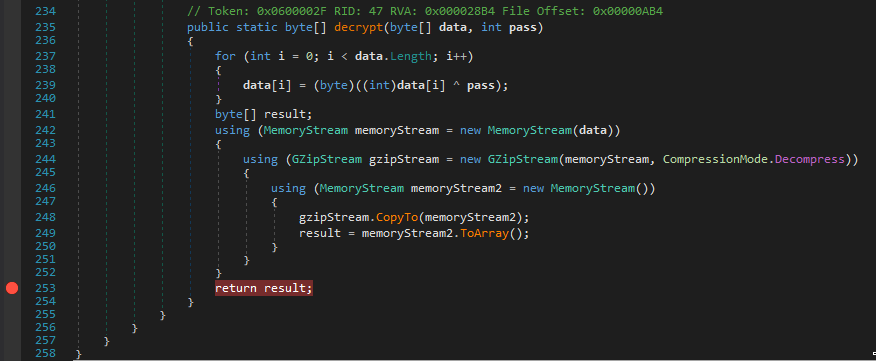
So I put a breakpoit at the return of the decrypt function and saved the result to disk. The function gets called twice, so I got two more files to look at.
file dump1.bin
dump1.bin: PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows
file dump2.bin
dump2.bin: PE32+ executable (DLL) (console) x86-64 Mono/.Net assembly, for MS WindowsAfter checking if these files contain the flag in plain text I stepped further through the code until the decrypted content got loaded as modules.
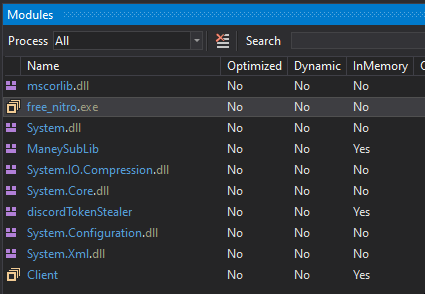
There are three new modules loaded into memeory. The only one which is not obfuscated is the Client.exe. So I looked at this one first. The Client.exe seems to take care of the basic C2 communication to exfiltrate data. My initial guess was that I need to find the Host we are tryng to connect to.
So the InitializeSettings() function where the hostname, port and some other stuff gets decrypted sound promising.
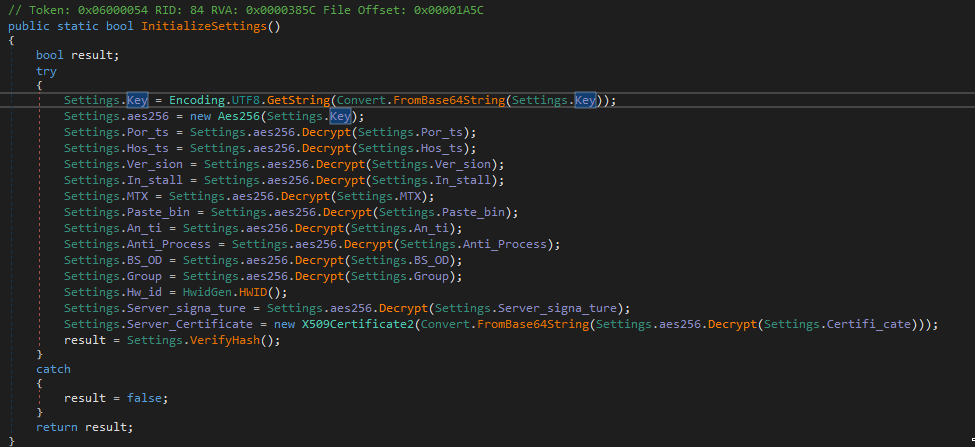
After hitting the breakpoint in the Initialize function I realized that the host and port was "REMOVED FOR SAFETY". Which makes sense since we are dealing with malware here :D
So i thougt this might be a dead end and I moved on to the discordTokenStealer.dll.
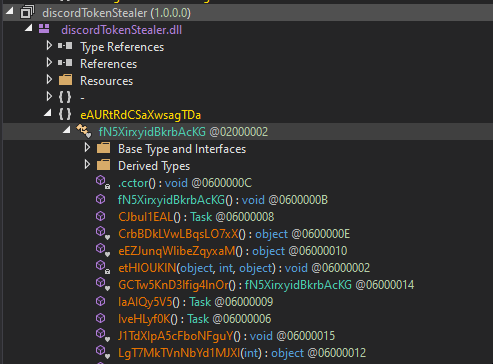
As it turned out this was a stupid idea. The discordTokenStealer.dll seems to be obfuscated and I wasted quite a bit of time reversing it. But as it turns out there is no flag in there either.
Solving it the right way
After the ctf ended I got a small hint on discord. As it turned out I was on the right track to look at the Client.exe. And also the InitializeSettings() was the right place to look at.
I guess I was just blind and tired.
So back to the Client.exe I checked out where the encrypted data like host, port and server_signature is stored. And look at this, there is also the encoded and encrypted flag…
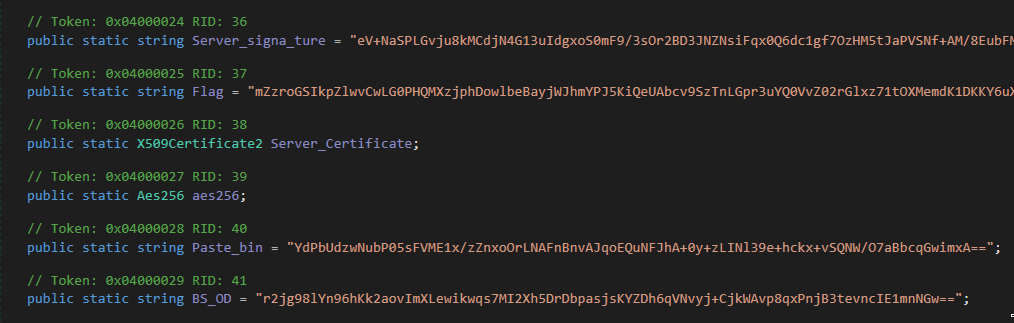
To decrypt the flag I places a breakpoint at the Decrypt function and replaced the input value by the ecrypted flag.
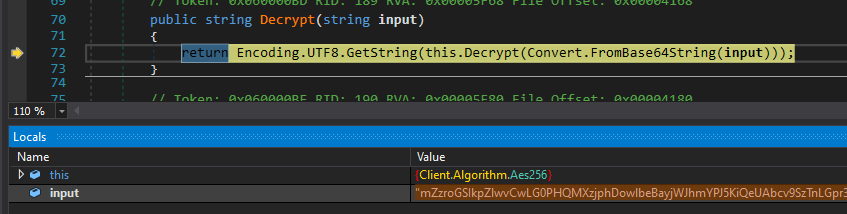
After hitting the next breakpoint which I placed at the point where the decrypted value is returned, I saved the return value to a file which contains the decrypted flag.
